FUTURE-PROOF ENCRYPTION
FOR THE QUANTUM ERA.
Achieve quantum resilience with
post-quantum cryptography and
crypto agility at your fingertips.
We Build the Tools to Counter the
Quantum Threat
STRENGTHENING DATA ENCRYPTION
High-speed Quantum Random Number Generator
CRYPTO-AGILE KEY MANAGEMENT
Flexible deployment of crypto algorithms

QUANTUM KEY DISTRIBUTION
Uses laws of physics to secure key distribution
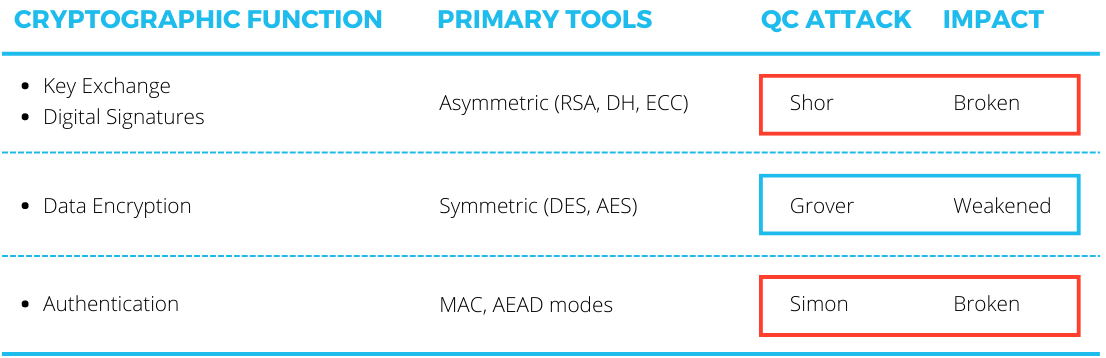
CAPABLE QUANTUM COMPUTERS
WILL BREAK PUBLIC KEY ENCRYPTION.
- No communication link will be trusted to be secure
- Communication would not be trusted to be authentic
- Transactions could be repudiated
CISOs should familiarize themselves with current quantum tech, start including quantum safe solutions in their lifecycle management, focus on improving crypto agility, and prepare for the implications of infinitely more powerful computers today.
FS-ISAC Insights: Martijn Dekker, Chief Information Security Officer, ABN AMRO
CAPABLE QUANTUM COMPUTERS
WILL BREAK PUBLIC KEY ENCRYPTION.

- No communication link will be trusted to be secure
- Communication would not be trusted to be authentic
- Transactions could be repudiated
MUCH CLOSER THAN THEY APPEAR
QUANTUM COMPUTERS THAT CAN BREAK PUBLIC KEY ENCRYPTION ARE CLOSER THAN YOU THINK
| OLD WAY OF THINKING | NEW REALITY |
| 1,000s of Stable Qubits | State Secret /New Algorithms |
| 1,000s of Stable Qubits | 100s of Stable Qubits |
| Classical Programming | AI and Machine Learning |
| 5-25 Years | 1-3 Years |
 |
 |
EVERY CRYPTO SYSTEM GETS BROKEN EVENTUALLY.
There is a clear and present risk to public key encryption. RSA will be broken in 1-3 years. If not by quantum computers, then by traditional silicon. It is coming. Public key encryption is at risk.
We can’t ignore 30 years of progress and assume Shor’s Algorithm is the only way to break encryption.
MUCH CLOSER THAN THEY APPEAR
QUANTUM COMPUTERS THAT CAN BREAK PUBLIC KEY ENCRYPTION ARE CLOSER THAN YOU THINK
| OLD WAY OF THINKING | NEW REALITY |
| 1,000s of Stable Qubits | State Secret /New Algorithms |
| 1,000s of Stable Qubits | 100s of Stable Qubits |
| Classical Programming | AI and Machine Learning |
| 5-25 Years | 1-3 Years |
 |
 |
EVERY CRYPTO SYSTEM GETS BROKEN EVENTUALLY.
There is a clear and present risk to public key encryption. RSA will be broken in 1-3 years. If not by quantum computers, then by traditional silicon. It is coming. Public key encryption is at risk.
We can’t ignore 30 years of progress and assume Shor’s Algorithm is the only way to break encryption.
If RSA was broken tomorrow…
What would you do?
In December 2022 there was a wakeup call that RSA 2048 could be broken with 300 Qubits. Not the 1m Qubits predicted. This Chinese research paper (which has since been debunked) touted a method in which they could use a much smaller (and currently available) amount of quantum computing power to break RSA.


New Super Computers

Small Quantum Computers
Artificial Intelligence

New Algorithms (Not Shor)

Public Key Encryption
What The Experts Think
“Because of ‘store now, decrypt later’ attack...the quantum threat should be taken into account before the question of whether the development of Cryptographically Relevant Quantum Computers will ever become achievable in the future is cleared up.”
| National Cybersecurity Agency of France (ANSSI) |
 |
“The anticipated cracking of encryption by quantum computers must be treated as a current threat. Any data stolen today that has been encrypted with a non-quantum resistant algorithms will eventually be accessible to an adversary with a large scale quantum computer.”
|
Chinese Threats |
 |
“America must start the lengthy process of updating our IT infrastructure today to protect against this quantum computing threat tomorrow.”
|
White House National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems (May 4, 2022) |
 |
“Your data is being harvested today, it will be breached tomorrow. Infrastructures, business and governments will be hacked and we won’t even know it.”
|
Interference Advisors & Quantropi “The quantum threat to our data & communications” |
 |
“The threat is that they copy down your encrypted data and hold on to it until they have a quantum computer.”
|
Dustin Moody, |
 |
“Organizations should inventory the most sensitive and critical datasets that must be secured for an extended amount of time. This information will inform future analysis by identifying what data may be at risk now and decrypted once a cryptographically relevant quantum computer is available.”
|
Dustin Moody, |
 |
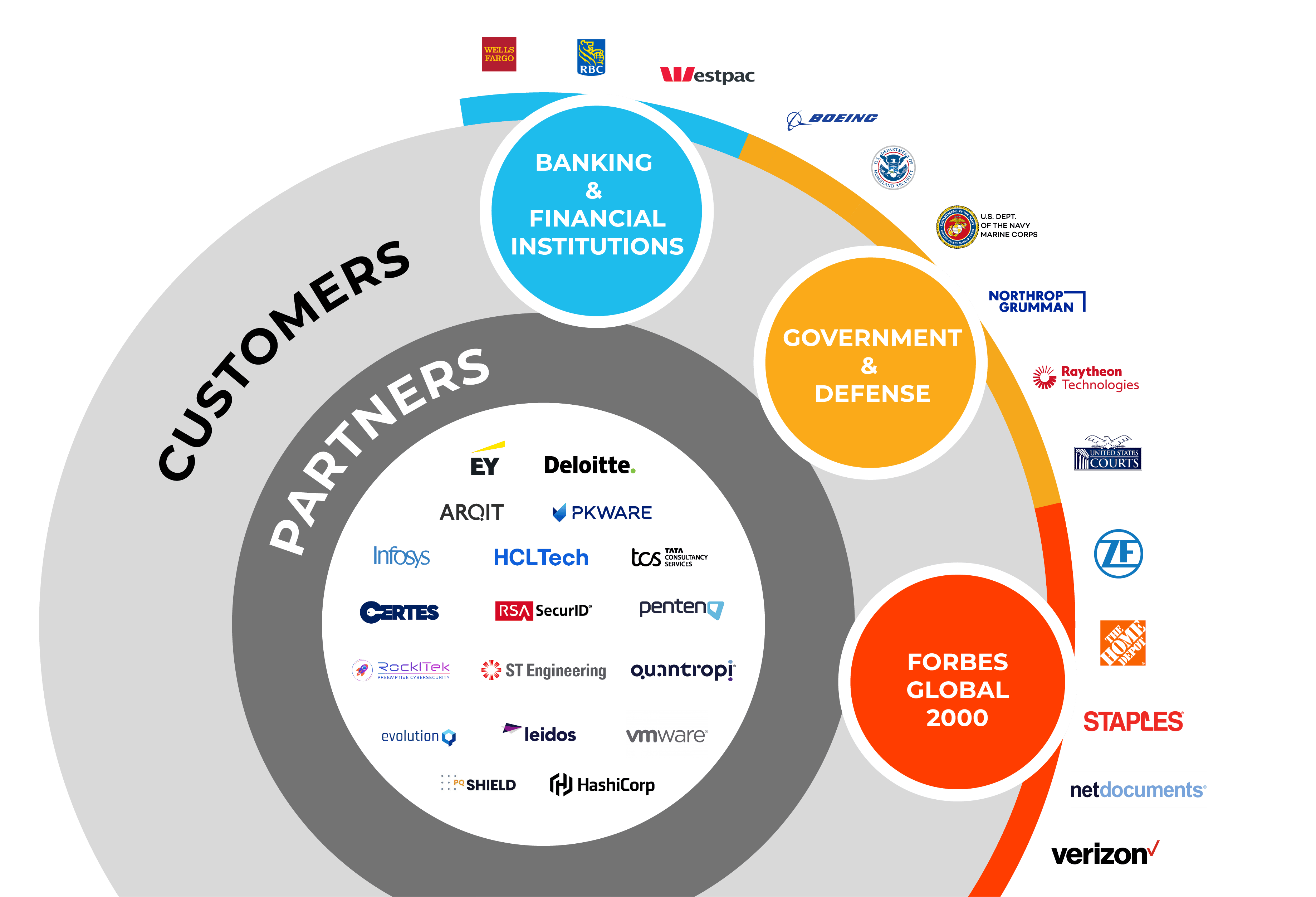
WINNERS ARE PICKING
TEAMS.
Why are these enterprises trusting QuintessenceLabs?
Because we’ve understood the whole problem since 2008.